In a world of digitalization, digital products have become an integral part of people's lives. The rapid growth of digitalization in the business environment unavoidably has become a magnet for public attention. With the increased use of the internet, every business firm uses the internet as a medium to reach its audience. And the internet world is never free from hackers. One of the biggest challenges that come in the way of a business firm is how to conduct online activities smoothly. How to keep their computer network secure from hacks? Also, speedy cloud adoption has its own set of risks and complexity of security obstacles.
Hackers constantly develop new ways to inroads to the computer network and access the important data. These data can be used for various illegal activities. This will lower the secrecy of the business organization. More than fifty percent of business firms around the globe deal with cyber-attacks.
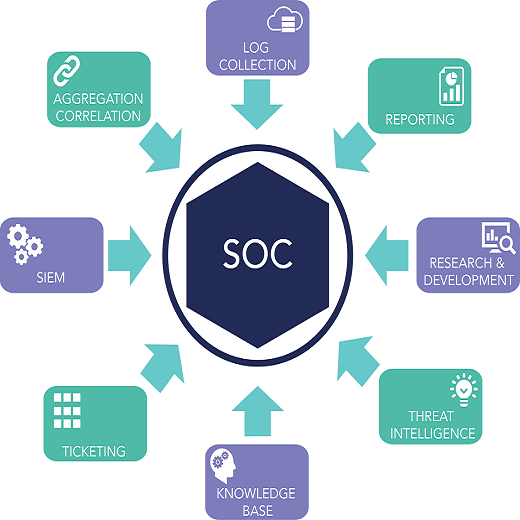
The need for a SOC as a Service (Security Operation Center)
Every organization is needed to have a team to fight against hackers. This will show significant growth in business affairs. The benefits of having a security operation center are as follows-
Centralized approach
The SOC team takes a lead when there is any breach or threat. The SOC as a Service team continuously keeps an eye on the entire network and any threat to the firm. They share the necessary information with the entire team members. This helps them to identify and counteract threats.
Cost control
The entire SOC team is located in one place. They monitor the activities of the business from a single location. This reduces the cost of hiring specialists who will be scattered at different locations. The firm needs to bear the cost of multiple rooms and other expenses. This will increase the recurring expenditure of a business.
Continuous proactive monitoring
The SOC team uses techniques that scan the network continuously. They keep a check on suspicious activities so that they can be detected at the earliest. Continuous check on the network allows the team to mitigate such threats. The advanced monitoring tools reduce the task of humans.
Log management
The SOC team is responsible for multi-task. They collect, maintain, and review the log of all network activity of an organization. They try to find a connection between those data collected from applications, firewalls, and operating systems. They identify the existing threats and can use remedies for such threats.

